LR-AKE
(Leakage-Resilient Authenticated Key Exchange)
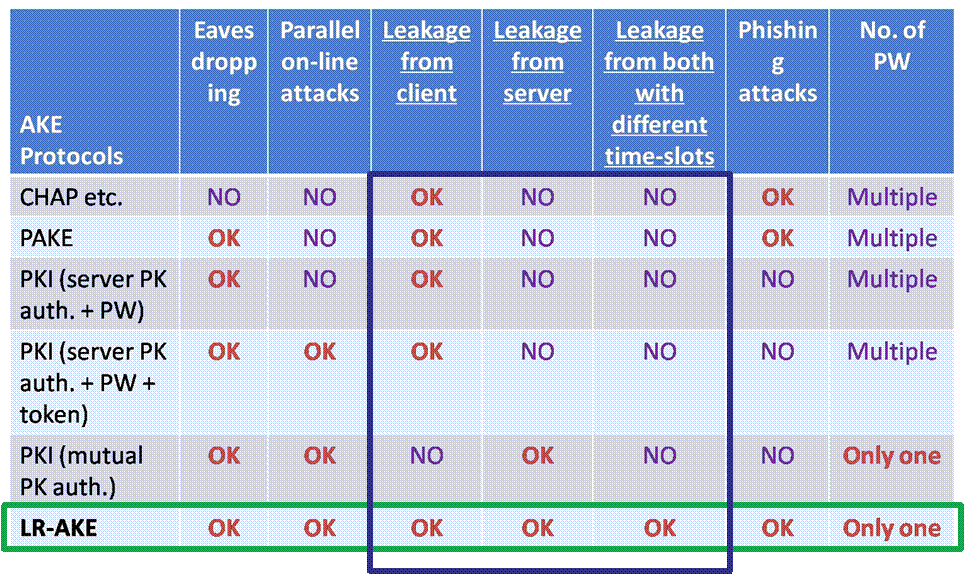
LR-AKE is a NEW authentication protocol where a user and a server authenticate each other and generate session keys in order to protect the subsequent communication channels between them. You can also see our papers.
| LR-AKE | Strong forward secrecy1 | Replacement attack2 | Server compromise impersonation attack2 |
|---|---|---|---|
| DL-based [SKI03,05] | Yes (with Secret-Values Update) | Not possible | Not considered |
| DL-based [?] | Yes | Not possible | Not possible |
| RSA-based [SKI07] | Yes | Not considered | Not considered |
| RSA-based [SKI10] | Yes | Not possible | Not possible (with Section 6.4) |
2: An attacker obtains server's stored secrets and then tries to impersonate the user, not the server. For more details, see [SKI10]. Another attack related to server compromise is server compromise server impersonation (for short, SCSI) attack where an attacker obtains server's stored secrets and then tries to impersonate the server. It is impossible for any AKE protocol to prevent the SCSI attack. However, DL-based LR-AKE provides security against the SCSI attack if the honest user and the honest server runs the LR-AKE protocol before the attacker impersonates the user or the server.
Relative leakage model considers side-channel attacks or cold-boot attacks where an attacker can get partial information about secrets. The constraint of this model is that the remaining information (after the partial leakage) about secrets should be at least in the security parameter (e.g., 80-bits). Contrary to relative leakage model, LR-AKE considers a different situation where an attacker can get all information about stored secrets. In such situation, LR-AKE is secure because the only possible attacks is on-line dictioinary attacks (i.e., the remaining secret information is a short password, remembered by the user).
[ADW09] J. Alwen, Y. Dodis, and D. Wichs, "“Survey: Leakage Resilience and the Bounded Retrieval Model", 2009